Risks and Challenges of Split Tunneling
VPN Split tunneling is a feature that allows users to divide their internet traffic into two distinct paths. While split tunneling offers numerous benefits, it also comes with certain risks and challenges that need to be considered. In this article, we will explore the risks associated with split tunneling and discuss the challenges that organizations may face when implementing this feature.
1. Increased Attack Surface
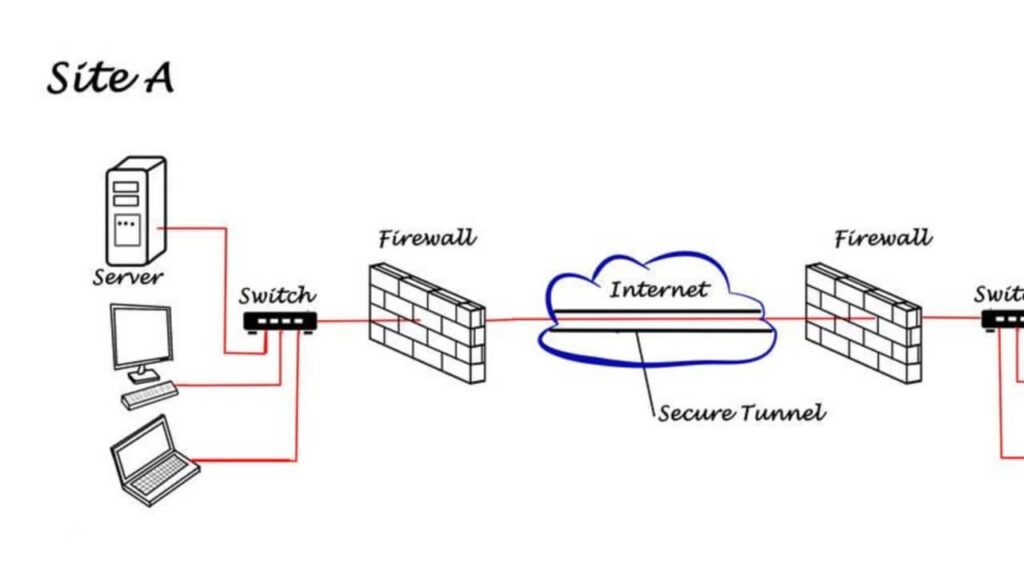
One of the main risks of split tunneling is the potential increase in the attack surface. When users direct certain traffic outside of the VPN tunnel, it bypasses the security measures provided by the VPN.

This can leave the non-VPN traffic vulnerable to various cyber threats, such as malware, phishing attacks, and data breaches. It is crucial for organizations to carefully assess the security implications of split tunneling and implement additional measures to mitigate these risks.
2. Data Leakage

Split tunneling introduces the risk of data leakage. If sensitive data is transmitted through the non-VPN tunnel, it can be intercepted or accessed by unauthorized individuals. This is particularly concerning when employees connect to public or insecure networks, such as coffee shop Wi-Fi, where the risk of data interception is higher. Organizations must educate their employees about the risks associated with split tunneling and enforce strict security policies to prevent data leakage.
3. Compliance and Regulatory Requirements

Certain industries, such as healthcare and finance, have strict compliance and regulatory requirements regarding data security and privacy. Split tunneling may pose challenges in meeting these requirements as it involves routing sensitive data outside of the secure VPN tunnel.
Organizations operating in regulated industries must carefully evaluate the impact of split tunneling on compliance and ensure that appropriate measures are in place to maintain data integrity and confidentiality.
4. Network Performance and Bandwidth Management
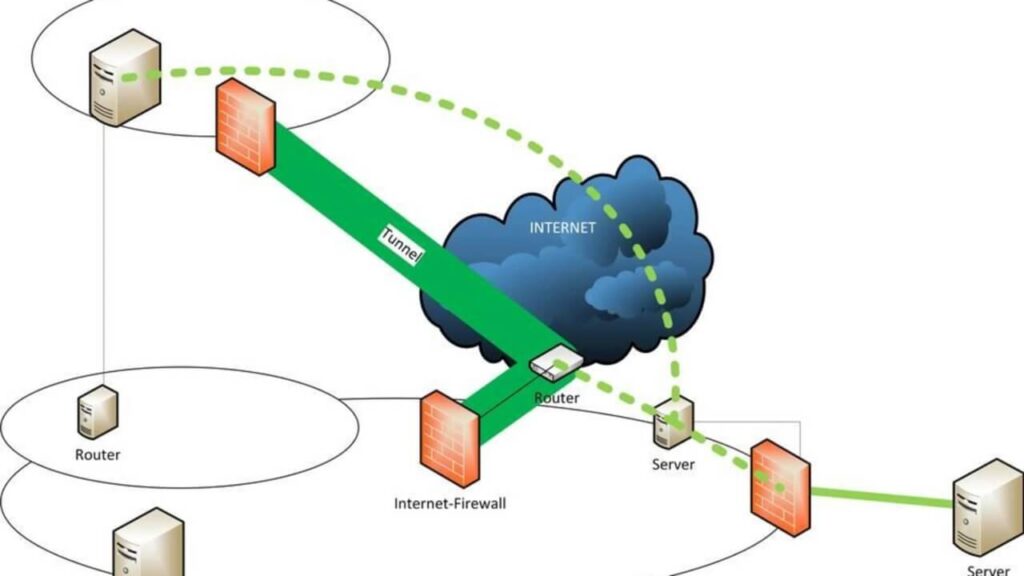
While split tunneling can enhance network performance by allowing non-sensitive traffic to bypass the VPN, it can also pose challenges in terms of bandwidth management.
If a large number of users direct bandwidth-intensive activities, such as streaming or downloading large files, outside of the VPN tunnel, it can impact the overall network performance and lead to congestion. Organizations need to implement effective bandwidth management strategies to ensure optimal network performance while maintaining security.
Best Practices for Implementing Split Tunneling
Implementing split tunneling requires careful planning and consideration of various factors. To mitigate the risks and challenges associated with split tunneling, organizations should follow these best practices:
1. Define Clear Security Policies

Establish clear security policies that outline which types of traffic should be routed through the VPN tunnel and which ones can bypass it. These policies should be based on the sensitivity of the data and the security requirements of the organization. Regularly communicate and enforce these policies to ensure consistent adherence.
2. Conduct Risk Assessments
Perform thorough risk assessments to identify potential vulnerabilities and risks associated with split tunneling. Assess the impact of split tunneling on data security, compliance requirements, and network performance. Use the findings of the risk assessments to develop appropriate mitigation strategies and controls.
3. Implement Multi-Factor Authentication

To enhance the security of split tunneling, implement multi-factor authentication (MFA) for VPN access. MFA adds an extra layer of protection by requiring users to provide multiple forms of authentication, such as a password and a unique code sent to their mobile device. This helps prevent unauthorized access to the VPN and reduces the risk of data breaches.
4. Encrypt Non-VPN Traffic

Even though non-VPN traffic bypasses the VPN tunnel, it is still important to encrypt this traffic to protect it from interception.
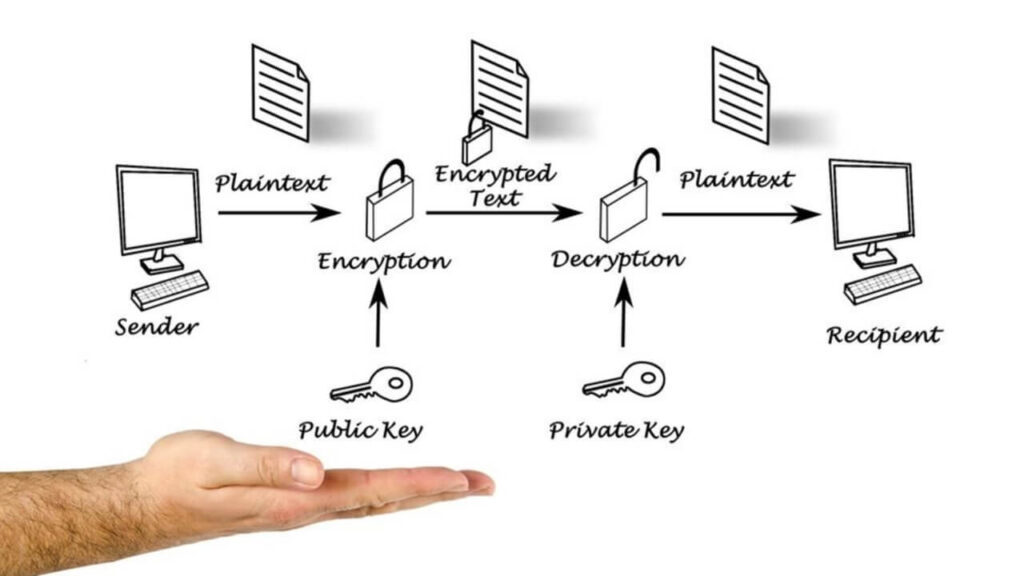
Implement encryption protocols, such as HTTPS, for non-VPN traffic to ensure the confidentiality and integrity of the data transmitted outside of the VPN tunnel.
5. User Education and Awareness

Educate employees about the risks and challenges of split tunneling. Train them on how to identify and avoid potential security threats when accessing the internet outside of the VPN tunnel. Promote awareness of best practices for secure internet browsing and emphasize the importance of adhering to the organization’s security policies.
In conclusion, while split tunneling offers benefits such as improved network performance and flexibility, it also introduces risks and challenges that organizations must address. By understanding and mitigating these risks through the implementation of best practices, organizations can leverage the advantages of split tunneling while maintaining the security and integrity of their data and network infrastructure.
























F*ckin’ awesome issues here. I’m very glad to peer your post. Thanks a lot and i am taking a look forward to touch you. Will you please drop me a mail?
Hello my friend! I wish to say that this article is amazing, great written and include approximately all vital infos. I?¦d like to see extra posts like this .
I don’t usually comment but I gotta state thanks for the post on this one : D.
I’ve been surfing online greater than three hours today, but I never discovered any interesting article like yours. It is lovely value sufficient for me. In my opinion, if all web owners and bloggers made excellent content as you probably did, the web shall be much more useful than ever before.
My husband and i got absolutely peaceful when Edward could carry out his basic research by way of the precious recommendations he came across from your own site. It is now and again perplexing to just continually be making a gift of methods most people could have been making money from. We consider we have got the writer to be grateful to for that. The main explanations you have made, the straightforward website menu, the friendships you make it possible to foster – it’s got most extraordinary, and it’s facilitating our son in addition to our family recognize that that theme is fun, and that’s tremendously indispensable. Thank you for the whole lot!
Thank you for sharing superb informations. Your site is so cool. I’m impressed by the details that you have on this website. It reveals how nicely you understand this subject. Bookmarked this website page, will come back for extra articles. You, my pal, ROCK! I found simply the information I already searched everywhere and just couldn’t come across. What an ideal site.
As I website possessor I think the articles here is rattling excellent, regards for your efforts.
F*ckin’ tremendous issues here. I am very satisfied to peer your article. Thanks a lot and i am having a look ahead to touch you. Will you kindly drop me a mail?
I simply could not go away your website prior to suggesting that I extremely loved the usual information an individual supply in your visitors? Is going to be again continuously to check out new posts.
Greetings from California! I’m bored to death at work so I decided to check out your blog on my iphone during lunch break. I love the info you present here and can’t wait to take a look when I get home. I’m shocked at how quick your blog loaded on my phone .. I’m not even using WIFI, just 3G .. Anyhow, superb blog!
What i do not realize is actually how you’re not actually much more well-liked than you might be now. You are so intelligent. You realize thus considerably relating to this subject, made me personally consider it from so many varied angles. Its like women and men aren’t fascinated unless it is one thing to do with Lady gaga! Your own stuffs outstanding. Always maintain it up!
Appreciating the persistence you put into your website and in depth information you present. It’s great to come across a blog every once in a while that isn’t the same outdated rehashed material. Great read! I’ve bookmarked your site and I’m adding your RSS feeds to my Google account.
I’m still learning from you, as I’m improving myself. I absolutely enjoy reading everything that is posted on your site.Keep the stories coming. I enjoyed it!
It¦s really a great and useful piece of information. I¦m glad that you just shared this helpful information with us. Please stay us up to date like this. Thanks for sharing.
Exceptional post but I was wanting to know if you could write a litte more on this topic? I’d be very grateful if you could elaborate a little bit further. Thanks!
I got what you intend, thanks for putting up.Woh I am happy to find this website through google.
Spot on with this write-up, I really assume this website wants much more consideration. I’ll probably be again to read rather more, thanks for that info.
I haven?¦t checked in here for a while as I thought it was getting boring, but the last few posts are good quality so I guess I?¦ll add you back to my everyday bloglist. You deserve it my friend 🙂
I really appreciate this post. I’ve been looking everywhere for this! Thank goodness I found it on Bing. You’ve made my day! Thank you again
very nice put up, i actually love this website, carry on it