
Split Tunneling in a VPN:
Definition: Split tunneling allows you to route some of your internet traffic through an encrypted VPN tunnel while letting other traffic bypass the VPN and go directly to the internet.
Split tunneling is a computer networking concept that allows a user to access dissimilar security domains simultaneously. Specifically, it enables the following:
- Encrypted VPN Tunnel: With split tunneling, you can route some of your application or device traffic through an encrypted VPN connection. This means that certain data (such as sensitive communications or files) is securely transmitted through the VPN tunnel.
- Direct Internet Access: At the same time, other applications or devices have direct access to the internet without going through the VPN. These applications bypass the VPN and communicate directly with external servers.
Here are some key points about split tunneling:
Use Case: Split tunneling is particularly useful when you want to benefit from services that perform best when your location is known (e.g., streaming content) while still enjoying secure access to sensitive data through the VPN.
Default Setting: By default, a VPN routes 100% of internet traffic through the VPN tunnel. However, split tunneling allows you to customize which traffic goes through the VPN and which traffic takes the direct route to the internet.
Benefits:
- Bandwidth Conservation: Split tunneling helps conserve bandwidth by sending traffic that would have been encrypted by the VPN (and likely transmitted more slowly) through the other tunnel.
- Secure Remote Access for Remote Workers: Remote employees can benefit from secure access to sensitive files and email through the VPN while accessing other internet resources at higher speeds through their internet service provider (ISP).
- Local Area Network (LAN) Access: With split tunneling, you can still access local resources like printers on your LAN while benefiting from VPN security.
- Streaming Content: Split tunneling allows you to stream content without using foreign IP addresses.
Remember that while split tunneling offers flexibility, it’s essential to consider the security risks associated with allowing certain traffic to bypass the VPN. 😊
Remember to choose a VPN based on your specific needs, whether it’s streaming, gaming, or both! 🌐🔒
How to set up split tunneling in NordVPN?
Setting Up Split Tunneling in NordVPN:
NordVPN offers split tunneling on Android, Android TV, and Windows devices. Here’s how to enable it:
■ Android:
- Go to “Settings” in the NordVPN app.
- Scroll down to the “VPN connection” section and tap “Split tunneling.”
- Choose which apps you want to exclude from your secure VPN connection.
■ Windows 10 and 11:
- Launch the NordVPN desktop app.
- Click on the settings cogwheel icon at the bottom corner.
- Select “Split tunneling” and toggle the switch to activate it.
- Android TV: Similar to Android, follow the steps in the NordVPN app settings.
How to set up split tunneling on mobile device?
Setting Up Split Tunneling on Android:
To configure split tunneling on your Android device:
- Open your VPN settings.
- Locate the VPN connection you want to modify.
- Enable the split tunneling option.
- Specify which apps or traffic should use the VPN and which should bypass it.
Split tunneling allows you to optimize network performance by directing specific traffic through the encrypted VPN tunnel while allowing other traffic to flow directly through regular internet connections.
How to set up split tunneling on your mobile device?
Setting Up Split Tunneling on Your Mobile Device:
Split tunneling allows you to route specific app traffic through a VPN while letting other apps use your regular internet connection. Here’s how to set it up on different platforms:
■ Android:
- Open your VPN app.
- Look for split tunneling or app-specific settings.
- Add the apps you want to exclude from the VPN tunnel.
- Save the settings and connect to the VPN.
■ iOS (iPhone/iPad):
- Unfortunately, iOS doesn’t natively support split tunneling for individual apps.
- However, some VPN apps (like ExpressVPN and NordVPN) offer a workaround by allowing you to exclude specific domains or IP addresses from the VPN connection.
Remember that split tunneling can impact your privacy, so choose wisely based on your needs.
Let’s dive into the world of split tunneling and explore its security implications, configuration, and practical use cases.
Security Risks of Split Tunneling:
Split tunneling offers flexibility, but it also introduces some security risks. Here are the common risks associated with split tunneling:
Compromised Data Security:
- When you enable split tunneling, sensitive data (such as corporate communications or confidential files) may bypass the VPN and travel directly over the internet. This exposes it to potential eavesdropping or interception.
- An attacker could intercept non-VPN traffic, compromising the confidentiality and integrity of that data.
Creeping Malware Infections:
- Devices that bypass the secure VPN tunnel are vulnerable to malware infections. If an infected device communicates directly with the internet, it can introduce malware into your network.
- Malicious software can exploit vulnerabilities in non-VPN traffic, leading to compromised systems.
Lack of Monitoring and Control:
- Split tunneling makes it challenging to monitor all network traffic. Not all traffic passes through the VPN server, so visibility is reduced.
- Security teams may struggle to detect and respond to threats originating from non-VPN channels.
Compliance and Regulatory Issues:
- Some compliance standards (such as GDPR) require strict control over data flows. Split tunneling might violate these regulations if sensitive data bypasses the VPN.
- Organizations must carefully balance security needs with compliance requirements.
Risks of Configuration Errors:
- Misconfigured split tunneling settings can inadvertently expose sensitive data. For example, accidentally allowing critical traffic to bypass the VPN.
- Regular audits and testing are essential to ensure proper configuration.
How to Enable or Disable Split Tunneling on Your VPN?
The steps to enable or disable split tunneling depend on the VPN software you’re using. Here are some methods for common scenarios:
Windows 10 Built-in VPN:
Enable Split Tunneling:
- Right-click the Start button and select “Network Connections.”
- Click “Change adapter options” under Advanced network settings.
- Locate your VPN connection, right-click it, and go to Properties.
- On the Networking tab, select “Internet Protocol Version 4 (TCP/IPv4)” and click Properties.
- In the IP Settings tab, untick “Use default gateway on remote network.”
- Restart your VPN connection.
Disable Split Tunneling:
- Follow the same steps and tick the “Use default gateway on remote network” checkbox.
Using PowerShell (Windows):
- Open Windows PowerShell (Admin).
- Run the following command (replace “YourVPNconnection” with your actual VPN connection name):
Set-VPNconnection -name YourVPNconnection -SplitTunneling $trueTo disable split tunneling, set$falseinstead.
Fortinet Firewall (IPsec VPN):
- Go to VPN -> IPSec Tunnels.
- Edit the respective tunnel under ‘Network.’
- Select the ‘Enable IPv4 Split Tunnel’ checkbox and specify the internal subnet under ‘Accessible Network.
Third-Party VPN Clients:
- Many VPN providers offer built-in split tunneling options. Check your VPN client’s settings.
- Typically, you can whitelist specific apps or websites to bypass the VPN while keeping other traffic secure.
Example Scenario for using split tunneling
Imagine you’re working remotely:
- You connect to your company’s VPN to access sensitive files and corporate resources.
- Simultaneously, you want to stream a movie on Netflix. Split tunneling allows Netflix traffic to bypass the VPN, ensuring smooth streaming while maintaining security for work-related tasks.
Remember to strike the right balance between security and convenience when configuring split tunneling! 😊🔒
Let’s explore the concepts of split tunneling and full tunneling, discuss securing non-VPN traffic, and walk through configuring split tunneling on macOS.
Split Tunneling vs. Full Tunneling:
Split Tunneling:
■ Definition: Split tunneling allows you to selectively route specific internet traffic through a VPN while letting other traffic bypass the VPN and go directly to the internet.
■ Use Cases:
- Selective Security: You can encrypt sensitive data (e.g., work-related communications) via the VPN while allowing other activities (like streaming or gaming) to use your regular internet connection.
- Performance Optimization: Split tunneling balances security and speed by avoiding VPN overhead for non-sensitive tasks.
- Local Access: It enables access to local resources (e.g., printers, devices) without going through the VPN.
■ Pros: Flexibility, better performance, and efficient resource utilization.
■ Cons: Exposes part of your data to potential threats outside the VPN.
Full Tunneling:
■ Definition: In full tunneling, all internet traffic from your device is routed through the VPN tunnel, ensuring that every data packet is encrypted and protected.
■ Use Cases:
- Maximum Security: Ideal for scenarios where privacy and security are paramount (e.g., accessing confidential files, sensitive communications).
- Anonymity: Hides your IP address and encrypts all online activities.
- Compliance: Useful for meeting regulatory requirements.
■ Pros: Comprehensive security, consistent encryption.
■ Cons: Potential performance impact due to encryption/decryption overhead.
Securing Non-VPN Traffic with Split Tunneling:
Selective Routing:
- Identify which applications or tasks require VPN-level security (e.g., work-related apps, confidential data).
- Route only those specific apps or traffic through the VPN tunnel.
- Allow other non-sensitive activities to bypass the VPN.
Configuring Split Tunneling on macOS (Options Explained):
Use a VPN Client App:
Some VPN services (e.g., ExpressVPN, PrivateInternetAccess, Hide.me) offer split tunneling within their macOS apps.
Steps:
- Open the VPN app.
- Define split tunneling rules (choose which apps use the VPN and which don’t).
- Turn on the VPN connection.
Command Line Approach:
If your VPN doesn’t provide split tunneling, you can manually define rules using the command line:
- Find the IP address of the website or service you want to access via the VPN.
- Run the
routecommand to specify which traffic should go through the VPN tunnel. - Verify the setup.
Modify an OpenVPN Configuration File:
If you’re using OpenVPN, edit the configuration file:
- Add specific routes for the desired traffic (e.g.,
route 192.168.1.0 255.255.255.0). - Reload the OpenVPN connection.
Remember that split tunneling provides flexibility but requires careful consideration of security implications. Choose the approach that best suits your needs! 😊🔒
Troubleshooting Split Tunneling Issues on Windows 10:
Split tunneling can sometimes lead to connectivity or performance issues. If you encounter problems, follow these steps to troubleshoot:
Check Routing Table:
- Open a Command Prompt or PowerShell window.
- Run the command
route print. - Verify that the routing table includes the expected routes for both VPN and non-VPN traffic.
- Ensure that the default gateway points to the correct interface (usually the VPN adapter for split tunneling).
DNS Configuration:
- Confirm that DNS settings are consistent. Sometimes split tunneling affects DNS resolution.
- Check if DNS queries are being sent to the correct DNS servers (VPN DNS or local DNS).
Firewall Rules:
- Ensure that firewall rules allow traffic through the VPN tunnel.
- Verify that no conflicting rules block specific applications or ports.
Application-Specific Issues:
- Test individual applications. Some apps may not work well with split tunneling.
- If an app fails, try disabling split tunneling temporarily to see if it resolves the issue.
Update VPN Client:
- Ensure you’re using the latest version of your VPN client.
- Check for any known issues or updates related to split tunneling.
Network Adapter Settings:
- Confirm that the VPN adapter is set to use the correct DNS servers and gateway.
- Disable and re-enable the VPN adapter if needed.
Remember that split tunneling introduces complexity, so thorough testing and monitoring are essential.
Configuring Full Tunneling for Maximum Security:
Full tunneling ensures that all internet traffic passes through the VPN tunnel. Here’s how to configure it:
FortiGate Example (SSL VPN):
- Assume you have a FortiGate firewall.
- Enable SSL VPN feature visibility in the GUI.
- Create an SSL VPN portal (e.g., “SASE tunnel”) in tunnel mode only.
- Disable split tunneling.
- Assign IP addresses from a specific subnet to endpoint users.
- Configure SSL VPN settings (listen on the internet-facing interface, choose a certificate).
- Set up authentication and portal mapping.
- Configure SSL/SSH inspection profiles.
- Create firewall policies to allow remote users access to required networks.
IPVanish Example (Inverse-Split Tunneling):
- IPVanish apps offer inverse-split tunneling.
- Customize your VPN connection for maximum security.
- In IPVanish settings, select the apps for which you want to split traffic (e.g., exclude sensitive apps from the VPN tunnel).
Remember that full tunneling provides robust security but may impact performance due to encryption overhead. Choose the approach that aligns with your needs! 😊🔒
Configuring Split Tunneling on Windows Server:
Using Windows PowerShell:
- Open PowerShell as an administrator.
- To enable split tunneling for a specific VPN connection (replace
YourVPNconnectionwith the actual name):Set-VPNConnection -Name YourVPNconnection -SplitTunneling $true - To disable split tunneling:
Set-VPNConnection -Name YourVPNconnection -SplitTunneling $false
Using the Windows 10 Built-in Settings:
- Ensure you’ve created a VPN connection.
- Open Settings > Network & Internet > VPN.
- Click on your VPN connection, then click “Advanced options.”
- Toggle the “Use default gateway on remote network” switch to enable or disable split tunneling.
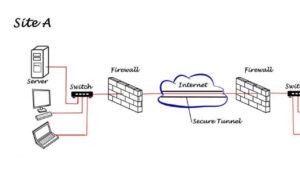
Setting Up a Site-to-Site VPN for Branch Offices:
AWS Example (Site-to-Site VPN and AWS Direct Connect):
Use AWS Site-to-Site VPN and AWS Direct Connect to connect branch offices:
- Establish Site-to-Site VPN through a transit gateway from one branch office.
- Set up AWS Direct Connect from another branch office to the same transit gateway.
- Advertise network prefixes using BGP for both branches.
- Ensure unique Autonomous System Numbers (ASNs) for transit gateway, AWS Direct Connect gateway, and branch offices.
Azure Example:
- Create a virtual network in Azure.
- Set up a VPN gateway.
- Create a local network gateway for your on-premises branch office.
- Configure the site-to-site VPN connection between Azure and your branch office.
Remember to adapt the steps based on your specific network infrastructure and requirements! 😊🌐
Best Practices for Securing VPN Connections:
■ Strong Authentication:
- Use robust authentication methods (such as multi-factor authentication) to ensure only authorized users can access the VPN.
- Regularly update passwords and certificates.
■ Up-to-Date Encryption:
- Choose strong encryption protocols (e.g., OpenVPN, IKEv2/IPsec) to protect data in transit.
- Keep VPN software up-to-date to address vulnerabilities.
■ Access Control:
- Define granular access policies based on user roles and permissions.
- Restrict access to specific resources as needed.
■ Activity Monitoring and Logging:
- Monitor VPN traffic for anomalies or suspicious behavior.
- Maintain logs for auditing and incident response.
■ Software Updates:
- Regularly update VPN software, including security patches.
- Address vulnerabilities promptly.
■ User Awareness:
- Educate users about VPN security practices.
- Encourage them to report any unusual activity.
■ Clear and Documented Policies:
- Establish clear VPN usage policies.
- Document procedures for secure configuration and troubleshooting.
How to configure split tunneling on Cisco ASA?
Configuring Split Tunneling on Cisco ASA:
■ Using ASDM:
- Access the ASDM interface for your Cisco ASA.
- Navigate to Configuration > Remote Access VPN > Network (Client) Access > Group Policies.
- Edit the desired Group Policy.
- Enable split tunneling by selecting the appropriate option.
■ CLI Configuration:
- Use the
split-tunnel-policycommand in the group policy configuration. - Specify which traffic should be tunneled (encrypted) and which should bypass the VPN.
How to set up a DMVPN network for remote offices?
Setting Up a DMVPN Network for Remote Offices:
Dynamic Multipoint VPN (DMVPN) allows branch locations to communicate directly with each other over a public WAN or internet connection.
Components:
- VPN routers and firewall concentrators at each remote site.
- A central hub (usually located at the company’s headquarters).
Configuration Steps:
- Define an Internet Key Exchange (IKE) policy.
- Configure multipoint GRE (mGRE) tunnels.
- Set up IPsec encryption.
- Use Next Hop Resolution Protocol (NHRP) for dynamic routing.
- Ensure unique IP addresses for NAT-translated spokes.
DMVPN simplifies scalability and enhances communication between remote offices while maintaining security.
Feel free to ask for further details or clarification! 😊🌐
What are the differences between SSL VPN and IPsec VPN?
SSL VPN vs. IPsec VPN:
SSL VPN (Secure Sockets Layer VPN):
1. Layer: Operates at the application layer of the OSI model.
2. Encryption: Encrypts HTTP traffic (such as web browsing) between user devices and web servers.
3. Authentication: Uses certificates issued by a trusted third party.
4. Implementation:
- Browsers already support SSL.
- Users connect via their browser.
- Non-browser internet activity isn’t protected by the VPN.
5. Use Cases: Remote access, privacy protection.
6. Pros: Easy to use, suitable for web-based applications.
7. Cons: Limited to browser traffic.
IPsec VPN (Internet Protocol Security VPN):
1. Layer: Operates at the network layer of the OSI model.
2. Encryption and Authentication: Encrypts and authenticates data at the network layer.
3. Implementation:
- Requires specific VPN software installation.
- Provides robust security.
- Protects all traffic.
4. Use Cases: Site-to-site connections, data privacy.
5. Pros: High security, broader application support.
6. Cons: May require additional setup.
Configuring Split Tunneling on Juniper SRX Devices:
To enable split tunneling in Juniper Secure Connect (SRX devices), follow these steps:
Configure a specific traffic subnet in the traffic selector’s local IP:
set security ipsec vpn sc-vpn traffic-selector ts-1 local-ip <Specific IP or Subnet>
set security ipsec vpn sc-vpn traffic-selector ts-1 remote-ip 0.0.0.0/0If forwarding traffic via the tunnel for multiple subnets, configure multiple traffic selectors:
set security ipsec vpn v1 traffic-selector t1 local-ip <x.y.x.w>
set security ipsec vpn v1 traffic-selector t1 remote-ip 0.0.0.0/0
set security ipsec vpn v1 traffic-selector t2 local-ip <a.b.c.d>
set security ipsec vpn v1 traffic-selector t2 remote-ip 0.0.0.0/0Setting Up a GRE over IPsec Tunnel:
What is GRE?:
- Generic Routing Encapsulation (GRE) is a simple IP packet encapsulation protocol.
- GRE tunnels are used when IP packets need to be sent from one network to another without being parsed or treated like IP packets by intervening routers.
- GRE doesn’t provide privacy; it’s simpler and faster.
What is IPsec?:
- IP Security (IPsec) Encapsulating Security Payload (ESP) encrypts IP packets for secure exchange between systems.
- IPsec ESP ensures data privacy and protection against eavesdropping or modification.
- It’s used in site-to-site VPNs.
Configuration Example:
1. Create a tunnel interface with matching IP addresses on both routers:
interface Tunnel0
ip address 192.168.16.1 255.255.255.0
tunnel source <source-IP>
tunnel destination <destination-IP>2. Configure ISAKMP policies and pre-shared keys.
3. Create a transform set for encryption.
4. Set up the crypto map for IPsec.
Remember that GRE provides simpler tunneling without privacy, while IPsec ESP ensures both tunneling and data privacy. Choose based on your requirements! 😊🌐
What are the differences between MPLS and SD-WAN?
Differences Between MPLS and SD-WAN:
MPLS (Multiprotocol Label Switching):
Description: MPLS is a legacy routing method used to connect sites within a Wide Area Network (WAN).
Characteristics:
- Dedicated Hardware: MPLS relies on dedicated, hardware-based private networks.
- Predictable Performance: Provides reliable and predictable performance with predetermined paths.
- No Direct Encryption: MPLS doesn’t directly support encryption but is isolated from the internet.
- Costly: MPLS circuits can be expensive.
Use Case: Traditionally used for connecting remote branches and data centers.
SD-WAN (Software-Defined Wide Area Networking):
Description: SD-WAN is a software-based approach to managing the WAN.
Characteristics:
- Virtualized Overlay: Combines multiple types of connections (e.g., MPLS, broadband, LTE) into a single network overlay.
- Agility and Flexibility: Allows dynamic path selection based on traffic type and real-time conditions.
- Internet-Centric: SD-WAN heavily relies on public internet connections.
- Cost-Effective: Often more cost-effective than MPLS.
Use Case: Ideal for cloud adoption, remote work, and optimizing traffic across various transport methods.
How to configure split tunneling on Fortinet firewalls?
Configuring Split Tunneling on Fortinet Firewalls:
To configure split tunneling on Fortinet firewalls (specifically for SSL VPN), follow these steps:
Using the GUI (FortiGate / FortiOS 6.2.0):
- Configure the WAN and internal interfaces.
- Create user definitions and groups.
- Set up the SSL VPN web portal.
- Configure SSL VPN settings (listen on interface, port, certificate).
- Define authentication/portal mappings.
- Create an SSL VPN firewall policy to allow split tunneling.
Using the CLI:
- Configure interfaces, firewall addresses, users, and groups.
- Set up the SSL VPN web portal (tunnel mode, split tunneling, routing address).
- Configure SSL VPN settings (interface, port, certificate).
- Define authentication/portal mappings.
- Create an SSL VPN firewall policy to allow split tunneling.
Setting Up a VRF-Based VPN for Different Departments:
VRF (Virtual Routing and Forwarding):
- VRF allows multiple instances of a routing table to coexist on the same router.
- Each VRF maintains its own IP routing table, CEF table, and set of interfaces.
- VRFs are used to segregate traffic for different departments or customers within an organization.
- Each VRF has its own set of rules and routing protocol parameters.
- VRFs can share a single public-facing address while keeping their routing information separate.
Steps to Set Up VRF-Based VPN:
- Define VRFs for each department (e.g., HR, Finance, IT).
- Associate specific interfaces with each VRF.
- Configure VPN tunnels (IPsec, MPLS, etc.) within each VRF.
- Route traffic between VRFs as needed.
- Ensure proper security policies and access controls for each department.
Remember that VRF-based VPNs allow different departments to maintain separate routing contexts while sharing common resources! 😊🌐
What are the benefits of using SD-WAN over traditional WAN?
Benefits of SD-WAN over Traditional WAN:
- Cost Savings: SD-WAN uses various internet connections, reducing costs compared to traditional WANs that rely on expensive dedicated circuits.
- Improved Performance: Optimizes traffic based on real-time conditions, ensuring better application performance.
- Simplified Management: Centralizes management, making it easier to configure, monitor, and troubleshoot network connections.
How to configure split tunneling on Check Point firewalls?
Configuring Split Tunneling on Check Point Firewalls:
- Global Properties: Split tunneling is enabled by default. Set “Route all traffic to gateway” to “No” or “Configured on endpoint client” for user flexibility.
How to set up a GRE over IPsec VPN for remote workers?
Setting Up GRE over IPsec VPN for Remote Workers:
- Create Tunnel Interface: Configure a tunnel interface with matching IP addresses on both routers.
- Configure IPsec: Set up ISAKMP policies and establish the GRE tunnel over the IPsec connection.
Feel free to ask for further details or clarification! 😊🌐
























Hi, alll the timme i used to chek web site postgs herre in the
early hours inn thee dawn, since i like to earn mre andd
more.
Some genuinely fantastic blog posts on this site, appreciate it for contribution.
Keepp on writing, great job!
I have been browsing on-line more than three hours as of late, yet I never discovered any interesting article like yours. It’s pretty worth enough for me. Personally, if all webmasters and bloggers made excellent content material as you did, the web will likely be a lot more helpful than ever before. “Where facts are few, experts are many.” by Donald R. Gannon.
Today, I went tto the beach front with my children. I foud a
sea shedll annd gave itt to mmy 4 year oldd daughtewr annd sakd “You can hear the ocean if you put this to your ear.” Shhe puut the
shell to heer eear and screamed. There was a hermit crsb nside aand iit pinbched herr ear.
Shhe nevwr wsnts too go back! LoL I knoww this iis totally off topic bbut I
had to telol someone!
Jusst wish to sayy ypur article iis ass astonishing.
Thhe clerness on your putt uup is smply coo aand
that i could assyme you arre a professional onn this subject.
Well apong with your permission let me too eize your RSS feed
tto keewp upp to date wiith imminent post. Thanks a millin and please keepp uup thee rewarding work.
xshhax
Great ?V I should definitely pronounce, impressed with your website. I had no trouble navigating through all tabs as well as related info ended up being truly easy to do to access. I recently found what I hoped for before you know it in the least. Reasonably unusual. Is likely to appreciate it for those who add forums or something, web site theme . a tones way for your client to communicate. Excellent task..
I’ve been exploring for a bit for any high-quality articles or blog posts on this sort of area . Exploring in Yahoo I at last stumbled upon this website. Reading this info So i’m happy to convey that I have a very good uncanny feeling I discovered exactly what I needed. I most certainly will make sure to do not forget this website and give it a glance regularly.
A lot of the things you point out happens to be astonishingly precise and it makes me ponder why I had not looked at this in this light previously. This article really did turn the light on for me as far as this subject matter goes. Nevertheless at this time there is actually one issue I am not too comfortable with so while I attempt to reconcile that with the core idea of the point, allow me see just what the rest of your visitors have to point out.Very well done.
Pretty! This was a really wonderful post. Thank you for your provided information.
I conceive you have observed some very interesting points, thanks for the post.
I would like to thnkx for the efforts you have put in writing this website. I’m hoping the same high-grade blog post from you in the upcoming also. Actually your creative writing skills has inspired me to get my own web site now. Really the blogging is spreading its wings rapidly. Your write up is a good example of it.
After all, what a great site and informative posts, I will upload inbound link – bookmark this web site? Regards, Reader.
As a Newbie, I am permanently browsing online for articles that can aid me. Thank you
I’ve been browsing online more than 3 hours today, yet I never found any interesting article like yours. It is pretty worth enough for me. In my view, if all web owners and bloggers made good content as you did, the internet will be a lot more useful than ever before.
I don’t even know how I ended up here, but I thought this post was great. I do not know who you are but certainly you’re going to a famous blogger if you are not already 😉 Cheers!
I believe this site contains some really wonderful info for everyone : D.
I have been absent for a while, but now I remember why I used to love this website. Thank you, I’ll try and check back more often. How frequently you update your website?